One of the “big” things of late is the push to have all websites use HTTPS to encrypt traffic to websites. As Stefan Stienne of The Verge noted in the may May 2018 article Google Chrome is removing the secure indicator from HTTPS sites in September:
Here’s a quick HTTPS refresher course: it’s a more secure version of HTTP, acting as a secure communication protocol for users and websites, making it harder for eavesdroppers to snoop on your packets. Your data is kept secure from third parties, so most modern sites are employing this technology, using Transport Layer Security (TLS) the underlying tech behind HTTPS, to do this.
What this means is that the URL bar (or omnibar, or whatever a web browser calls it) will change (using Google Chrome as the example):
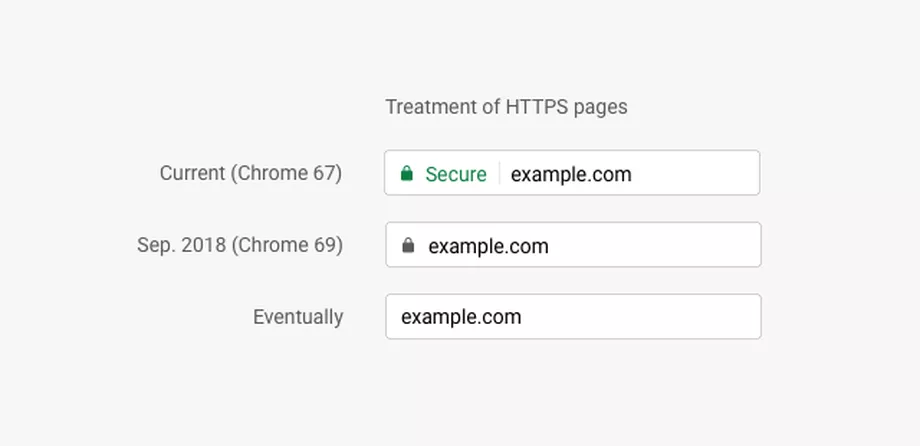
Eventually it will be:
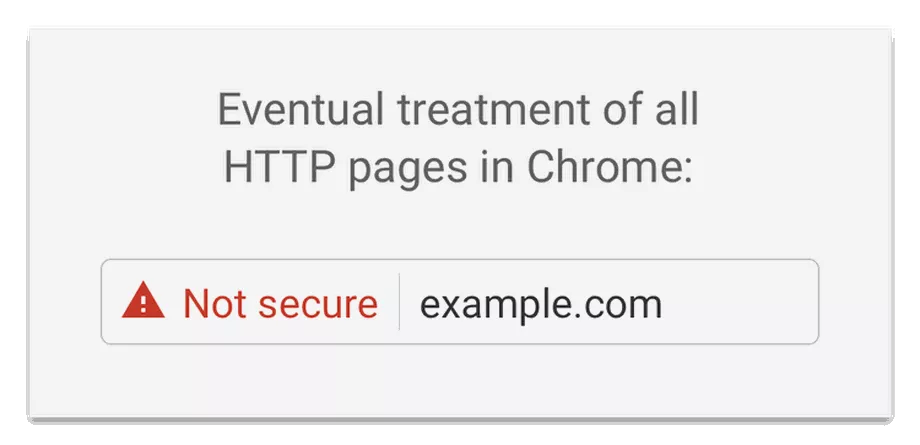
In on sense, this is somewhat agreeable. It will ensure that no one can easily snoop what is going back and forth when you connect to a website. That being said, nothing will stop an organisation breaking the TLS chain using a proxy and installing their valid SSL certificate in your browser’s certificate store. Since this certificate is self-signed, the client would receive an SSL warning message. Once the client installs the proxy’s certificate to let the browser trust the certificate, browsing websites with HTTPS will look normal and have the green padlock or no warning in the future (secure connection) in the URL bar. This works by:
client <===HTTPS===> proxy <===HTTPS===> server
^ ^
proxy certificate server certificate
So, unless you actually go and validate the certificate source you can still have your traffic sniffed. Many companies use SSL proxies to ensure that confidential information is not being leaked (assuming SSL decryption is being used for moral, lawful purposes). Of course I, for one, would not be surprised if something like the “Great Firewall of China” is not doing this (of course, law – and culture in some ways – comes into play here, too).
Of course, DNS servers will still know where you are going – you need to resolve an address to an IP address.
Secure Does Not Mean Trusted
All this does not mean that you should trust a website just because communications are encrypted! Anyone can get a Domain Validated (DV) certificate.That’s the way that Let’s Encrypt works. Now, I am not knocking Let’s Encrypt – I use it myself (see URL bar above).
This article on the types of certificates. Higher level certificates such as Organisation Validation (OV) and Extended Validation (EV) are a help. OV has more human intervention in the Certificate Authority (CA) validating that an actual business/organisation is reputable. This puts the organisation’s name in the certificate information. This costs money. EV certificates includes the most effort in validating a business/organisation reputation including extra documentation (See EV SSL Requirements). This costs more money and time. Chrome used to include the organisation’s name in the URL bar (it stopped doing so – I haven’t spent time finding out when but it was before Chrome 66) but Firefox, Internet Explorer and Microsoft Edge still do.
The problem is:
HTTPS ≠ TRUSTED
The website your are connecting must be trusted. Is the site trying to steal your credit card information? Is the site trying to get your personal information for spear phishing purposes? Just because the connection is encrypted (and may be doing so for other purposes than trying to make you think that their site is “trusted” – they may also be encrypting traffic to keep people from knowing what they are up to) does not mean you should trust the site!
That responsibility is up to you, dear reader. You need to determine if the site you are entering your credit card or other information is trustworthy. This means, for Chrome at least, you need to look at the certificate and determine if it is truly trustworthy. You need to look at the URL and make sure that it is really the website you are intending to visit – making sure that mybank.com isn’t actually mybonk.com.
Summing Up
Some of the good things about HTTPS everywhere is that it can (not will) help in keeping others from sniffing credit card or other personal information from your connection. Google’s eventual change of not identifying HTTPS and highlighting HTTP should help people understand when their communications can be read by other (or, maybe not so easily read is more accurate).
All that said the trust, the reputation, of where you are connecting is still up to you.
