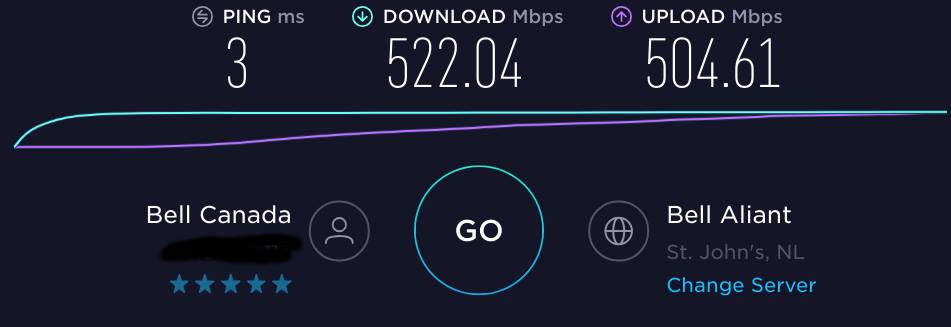
Wow! Two posts in two days 🙂
The second network upgrade was on the WiFi side of things. Again, I am blaming this on Tom Lawrence‘s YouTube channel where he reviewed the Ubiquiti access points. As I noted in Part 1, I had two access points in place – an Netgear EX6200 with OpenWRT and a stock Asus RT-N65U. (The reason why the RT-N65U was using stock firmware is that because of the chipset used, it does not seem that there is any maintained alternative firmware.)
The reason behind the EX6200 running OpenWRT is that I wanted a guest WiFi network for when friends and family come over. Not that I don’t trust my friends and family – I just don’t know if they practice safe computing. Plus, I wanted to implement VLANs.
It may sound “strange” that I have not put in VLANs previously, the fact is that it was an “around to it” task (actually, I did have it in place about 20 years ago but that old Nortel 10 Mbit/s 5-port switch gave up the ghost about 18 years ago). What I have been using was unmanaged* switches connected to router-based ports (e.g., each port was the gateway for their respective subnets). While this works, it does seem consume a lot of cables and switches without much flexibility 🙂
To get the guest WiFi network up-and-running, I needed VLANs because it didn’t seem that there was any easy way have guest access blocked to the home network without VLANs. Or have a separate guest access point (no…). (Yes, the guest WiFi only being able to access the Internet works when, for example, the RT-N65U is running as a router and a WiFi access point, but if you put it in access point mode that ability disappears.)
So, back to Tom Lawrence’s reviews of the capabilities of the the Ubiquiti UniFi access points. I was impressed! It works, well professionally. It is not quite as, I guess good is the word, as say a Cisco Meraki system, but it is nowhere near as expensive.
I settled on the UniFi AC AP Lite. The coverage is so good it replaced both the RT-N65U and the EX6200. It was easily mounted on the ceiling plus the PoE meant that I didn’t need to worry about where to plug in that wall wart power adaptor. I am seriously thinking about adding a second AC AP Lite in the future.
But the real icing on the cake is the UniFi Controller software. This can be an appliance with their Cloud Key product but will nicely run on a PC or a server. Or, in a Docker container – jacobalberty has a nice distro on Docker Hub and Crosstalk Solutions has a nice YouTube video tutorial on how to set it up on a Synology NAS Docker container. (See previous posts on my selection of Synology for two of my NASes.) The UniFi Controller does not have to up all the time (but if it isn’t you can’t really make any changes and some features are not available) but since a NAS is likely to be running all the time it is a good fit. I will say that you should watch the full Crosstalk Solutions video where it shows how you can have the configuration saved on the NAS so that when you upgrade the UniFi controller without having to restore your configuration.
I really like the ability to define you networks on the UniFi Controller and it is propagated through all the UniFi devices. Nice and easy software defined networking!
And since it was so nice… Well… Stay tuned for Part 3…
*unmanaged is apparently not a real word. And neither is untrusted (it is distrusted) – but what do I care?